Moving Beyond the Ethereum Phase of Security Tokens
As Originally Published on hackernoon.com
One of the existential debates in security tokens is what I often refer to as the generalists versus specialists debate. You’ve heard the arguments before: will we have one cryptocurrency or many? One blockchain or many? Public or permissioned?…The potential answer to those questions are the foundation to different school of thoughts in the crypto ecosystem and they permeate over all sub-segments of the industry. In the case of security tokens, we are starting to see versions of these existential crypto-debate:
· Will we have blockchains specialized on security tokens?
· Will security tokens work on public or permissioned blockchains?
· Should we build specialized security token networks?
· ….
It is extremely rare to see such a small technology market with such fragmented schools of thought. Part of the issue is that the security token market has involuntarily inherited some of those debates from the parent crypto-ecosystem. In the case of security tokens, the fragmentation debate expands across all layers of the ecosystem. Specifically, the digital securities market is venturing into a phase in which we are likely to see the emergence of tier 1 blockchains, tier 2 network in addition to the large number of existing security token platforms.
Blockchains, Networks and Tokens
A simplistic view of a technology market is a two layer structure with an infrastructure tier and an application tier. In that model, the infrastructure tier provides the generic building blocks for applications in the space while the applications tier enables domain specialization. In reality, technology markets are much more complex with several levels of infrastructure needed before we achieve any relevant specialization at the application layer.
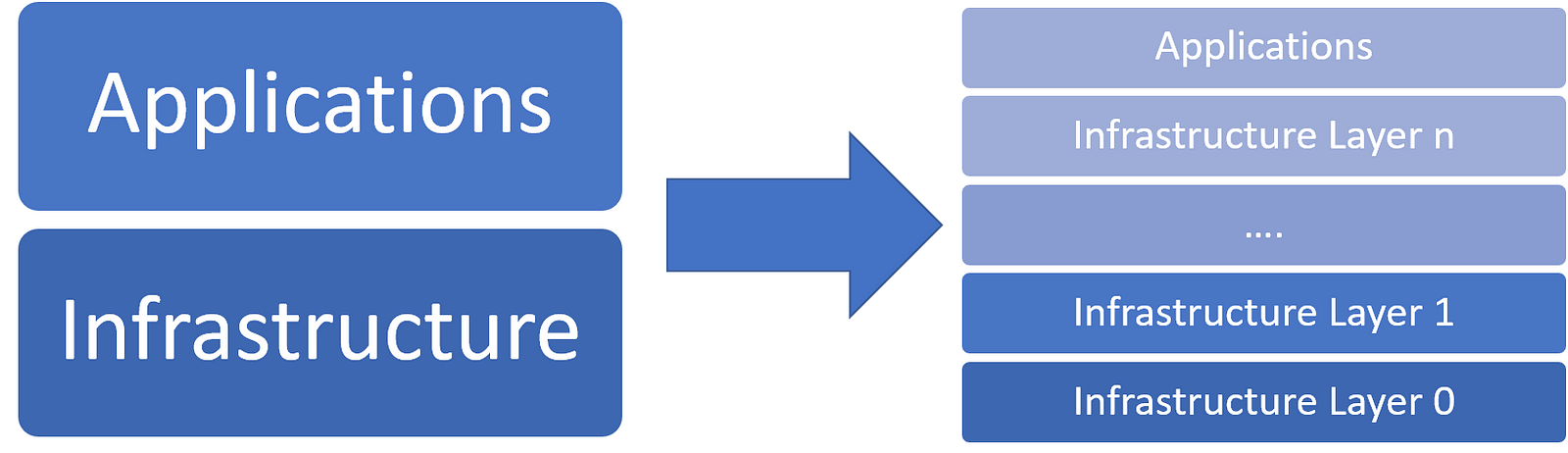
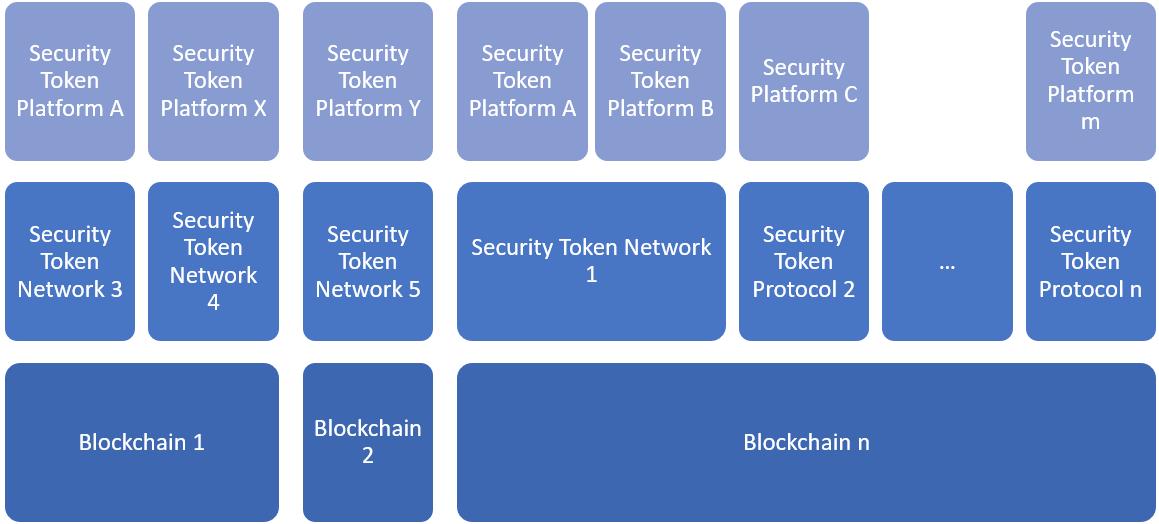
In the case of security tokens, the current ecosystem can be modeled in three fundamental layers:
· Blockchains: The infrastructure that provides the consensus, transaction validation and ownership transfer protocols for security tokens.
· Networks: Tier 2 infrastructure block that abstract the interaction between relevant parties in a specific digital securities transaction.
· Tokens & DApps: Specific security tokens or applications that leverage the other infrastructure tiers.
While security tokens started mostly as a variation of the Ethereum ERC-20 tokens, in just a few months we have seen aspiration projects like PolyMesh and Ownera evangelize the need for a security token blockchain and efforts like Provenance gain some traction for the implementation of security token networks. If that trends continues, we are likely to see an increasing level of fragmentation across different areas of the stack. Even though we are in the very early days of the digital securities markets, some of the fragmentation is already visible and has open the door to interesting possibilities in the near future:
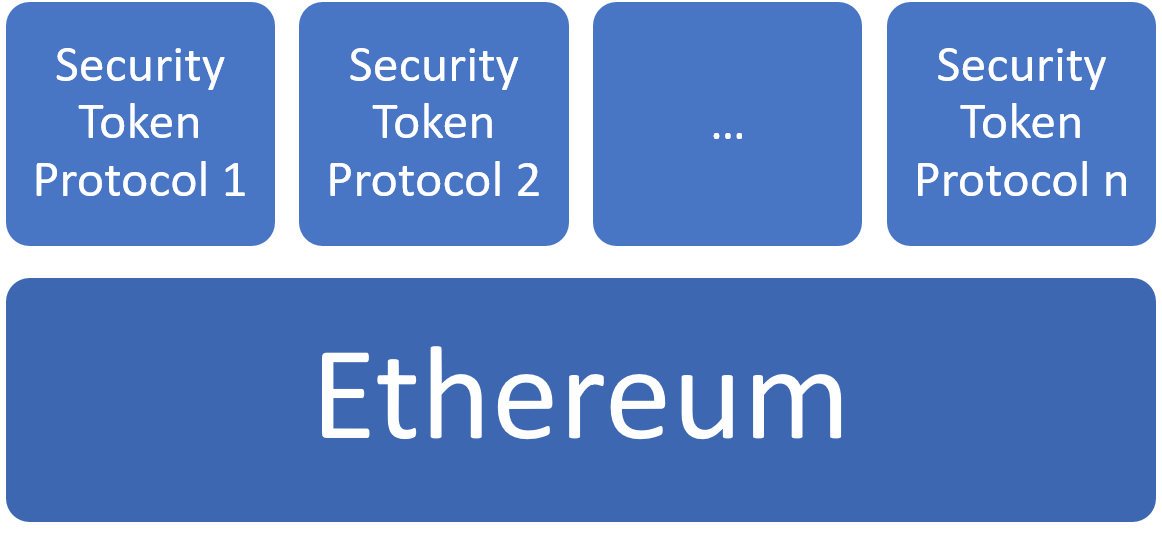
Ethereum for All
The most adopted approached among security token technology providers is to leverage Ethereum as the main blockchain runtime. Ethereum brings numerous advantages to digital securities including programmability, a rich ecosystem of protocols and tools and a growing developer community. However, leveraging a public blockchain for regulated securities introduces serious challenges in areas such as privacy, access control and scalability.
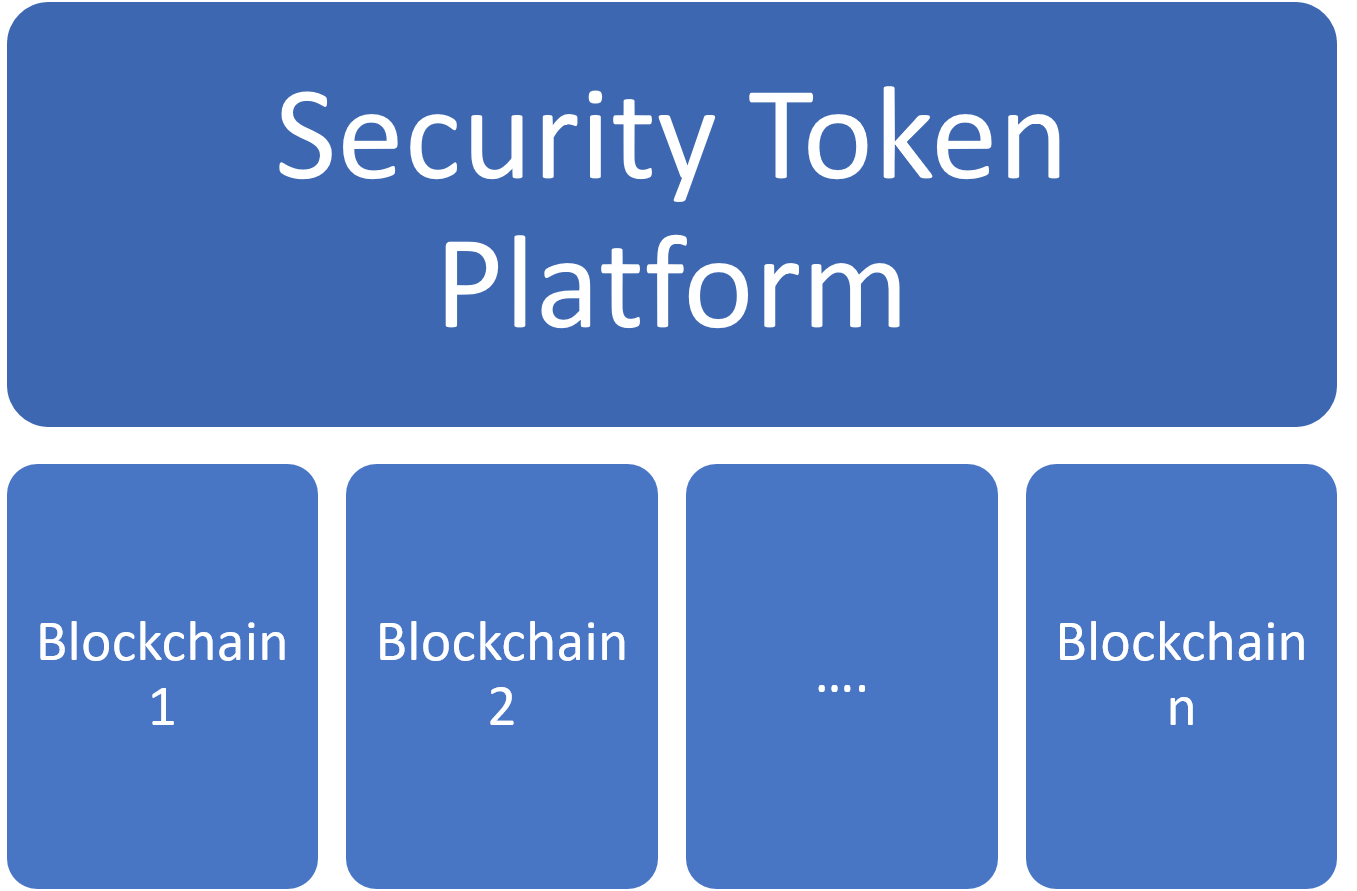
Many Blockchains, Generic Security Token Platforms
As security tokens evolved, we are witnessing an increasing interest of Ethereum competitors to enter the space. Public blockchains such as Cardano, Algorand or Tezos as well as permissioned alternatives such as Quorum or Hyperledger Fabric have slowly started initiatives related to digital securities. In that setting, we can envision security token platforms that enable blockchain-specific protocols but provide a consistent tooling and token lifecycle management stack. Consistency might be a strong advantage of this model. However, there is only so much that you can abstract from different blockchains without sacrificing functionality which might be the biggest drawback of this approach.
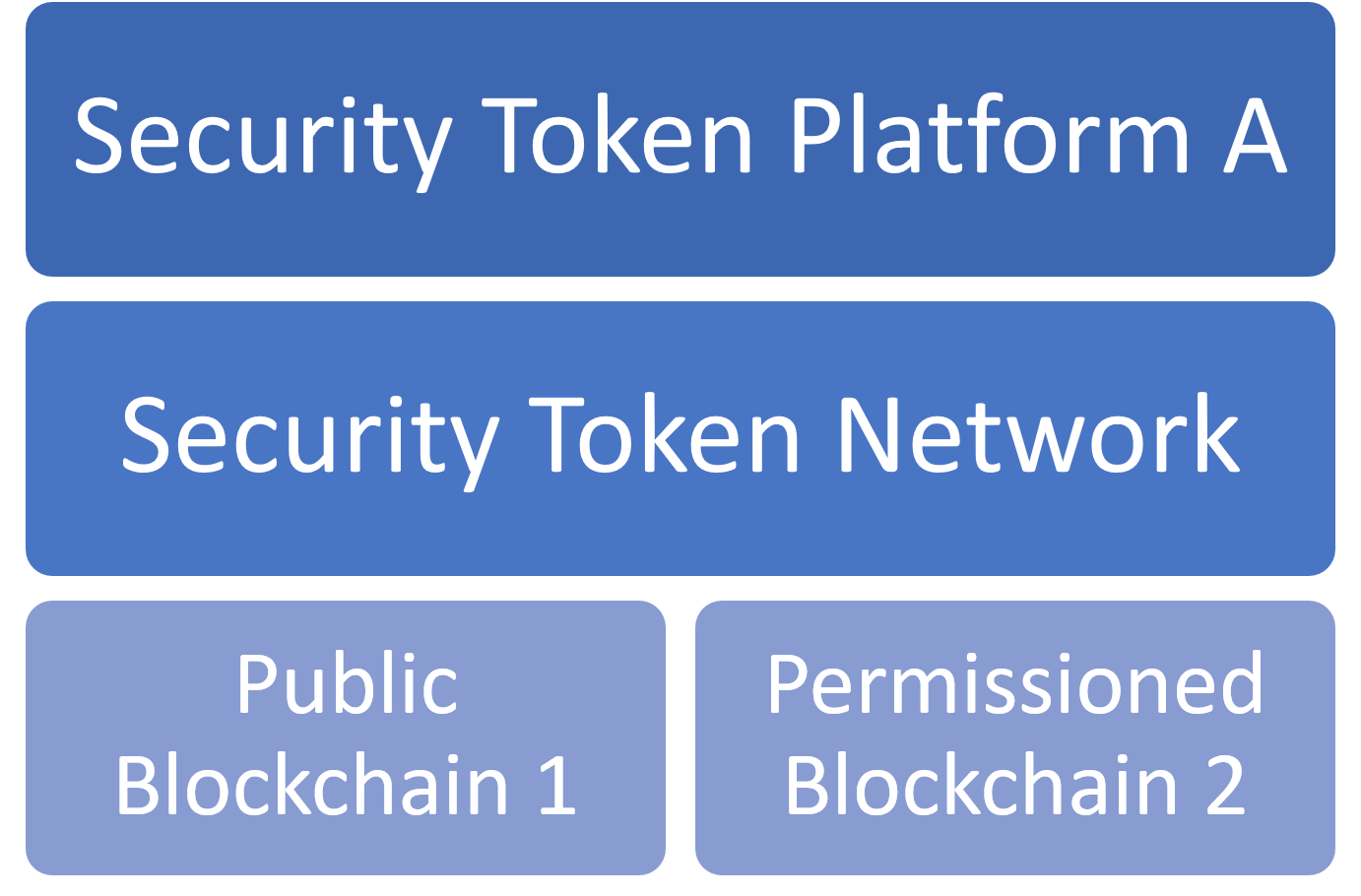
One Blockchain, Many Networks
The concept of security token networks such as Provenance or Ownera built on top of tier 1 blockchains seems to be gaining some traction although we still need to see in practice at a decent scale. This model seems to be more applicable to permissioned blockchain architectures such as Hyperledger Fabric or Quorum. If we assume that there will be a dominant blockchain for security tokens powering several networks for different digital securities products. The domain-specialization of security token networks makes it an interesting approach for creating long-tail network effects for security tokens. However, security token networks are still dependent on the dynamics of the underlying blockchain which introduces interesting challenges from a technical standpoint.
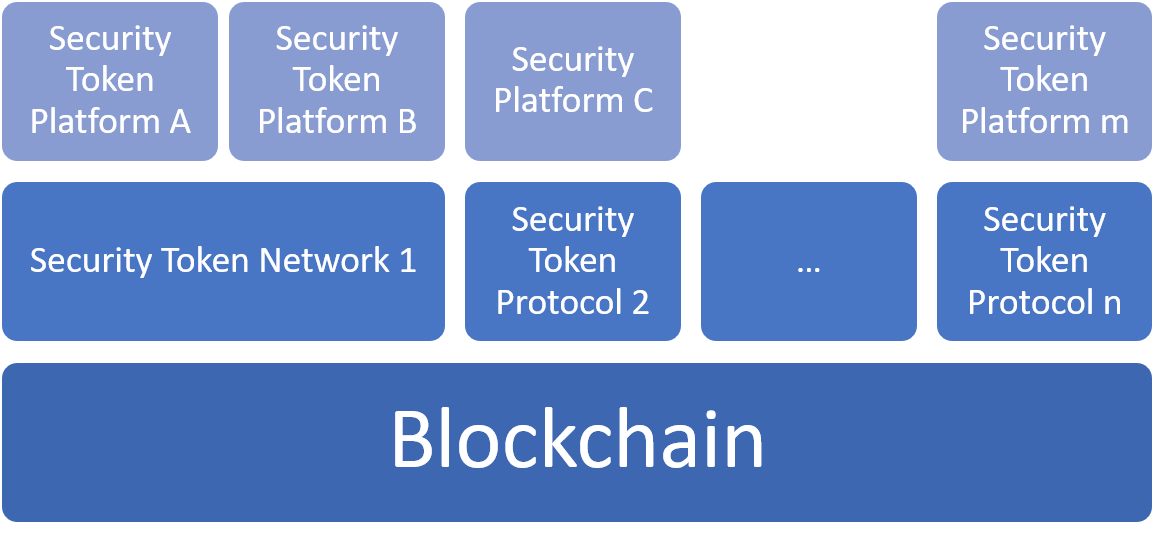
Many Blockchains, Many Networks
The previous model can evolve into a scenario in which we have many tier 1 blockchains and tier 2 security token networks across the entire ecosystem. This model inherits of the challenges of the previous approach in an even more fragmented ecosystem.
Hybrid Security Token Networks
I am very intrigued by the concept of security token networks that operate cohesively across public and permissioned blockchains. Similarly to the hybrid cloud model in cloud computing platforms, this approach could have nodes in a security token network operating in public blockchains like Ethereum or in permissioned alternatives such as Quorum. The clear advantage of this model is the combination of the privacy and access control capabilities of permissioned blockchains with the wide access and programmability of public blockchains.
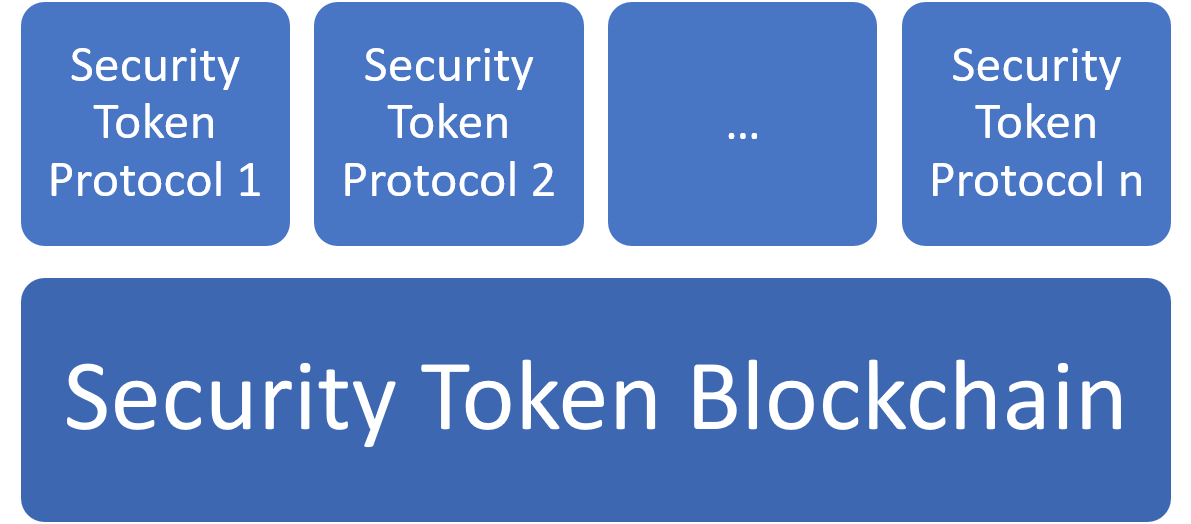
A Security Token Blockchain
The idea of a blockchain specialized in digital securities is as intriguing as it is questionable. In the past, I’ve written several articles about the arguments in favor and against a security token blockchain. Regardless of which side of the argument you sit on, we can all agree that security token blockchains might become a step in the evolution of the market.
The Capital Access Challenge
Most of the topologies outlined in the previous sections remain highly theoretical exercises without a viable path to market. Access to capital remains one of the biggest obstacles for the next phase of the infrastructure in security tokens markets. The implementation of security token blockchains and networks is a capital intensive exercise from both the technological and go-to-market standpoints. Until venture money starts flowing into the security token space, the infrastructure efforts will be led by a handful of companies that have better access to capital markets. Similarly, if venture investments in the digital securities space continue to be this moderated, the early infrastructure building might be able to gain a significant competitive advantage that will be really hard to disrupt.
By now, its pretty clear the we are moving beyond the Ethereum phase in the security tokens market. The next iteration of the market will bring Ethereum competitors in the ecosystem as well as the implementation of the first set of security token networks and blockchains. However, with limited interest from the venture community, those efforts might remain constrained to a small number of well capitalized companies.

