The Three Pillars Of Security Token Adoption
As Originally Published on thetokenist.io
In his new piece titled Blockchains, Networks, Protocols or Fantasies in Security Tokens: Part I, analyst Jesus Rodriguez outlines three fundamental approaches the security token industry needs moving forward. In the long-term, the space will need to develop its own blockchains specializing in tokenized securities.
According to Rodriguez, we “don’t yet understand what capabilities will be needed beyond [our current] point.” He spells out what the future might look like in his new piece.
The Three Fundamental Approaches
There are three security token infrastructural approaches which Rodriguez believes are most viable for the future. Each has their pros and cons, but the best option, he says, is for security tokens to have their separate blockchains. Simply put, existing public blockchains like Ethereum cannot resolve all of the compliance questions without major hiccups along the way.
Thin Protocols
Thin protocols are one option Rodriguez mentions in his piece. These would likely be run on the Ethereum blockchain and generally address compliance, identity, or financial primitives. This would be the first phase or ‘tier 1’.
Security Token Networks
The second possible phase would rely on having these security tokens on separate networks, with public blockchains like Ethereum providing the fundamental infrastructure. This can be done through sidechains. Rodriguez cites Provenance or Bumbiont as possible “tier 2” networks specializing in digital securities.
Security Token Blockchains
The final step, these would be standalone distributed ledger systems specializing in security tokens. We have already seen such efforts from Blockstream, Polymath, and others.
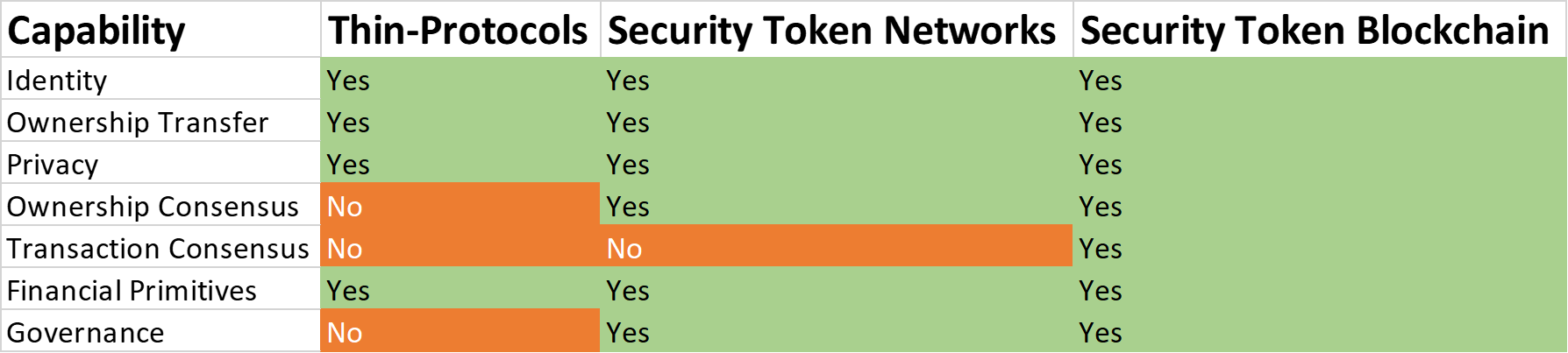
Of course, security token blockchains would require an altogether new mode of consensus. It would have to incorporate strictly compliant KYC procedures along with lawful transfer or ownership of assets.
The Future Moving Forward
Currently, we have barely scratched the surface of tier 1, but all of these three tiers are happening simultaneously. However, as the security token space develops, issuers will realize that separate blockchains specializing in security tokens are necessary. After all, the strict legal requirements mean that it is largely inevitable. The question is, how soon can the industry create such systems?
As of now, we’re still in the beginning stages.